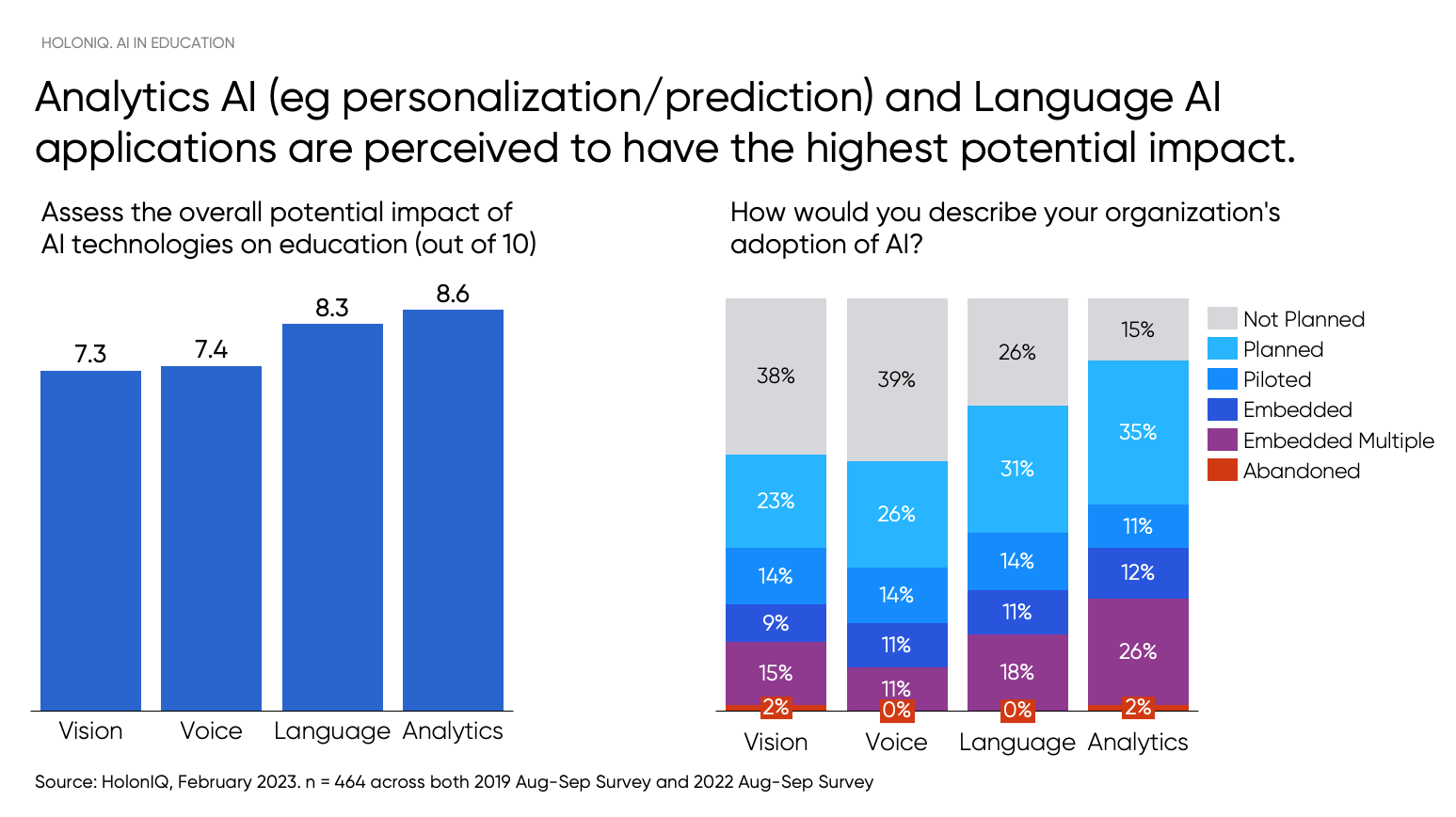
Decoding AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ: A Deep Dive into Its Significance
The digital landscape is littered with strings of seemingly random characters. These alphanumeric sequences often serve as vital keys. They unlock access to a vast array of online resources. One such string is AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ. This article will decode its significance. It will explain its purpose and function. We will explore its implications in the context of modern technology. We will also delve into the importance of security surrounding it.
Understanding the Fundamentals of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ
AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is a specific identifier. It is not a generic term. It is a unique string. It is typically associated with a particular service. Its function is to authenticate and authorize access. It ensures that only authorized users can access specific resources. This is a crucial aspect of online security. It helps prevent unauthorized access. This prevents potential data breaches and misuse.
The structure of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ often follows a specific format. This format is designed for security and efficiency. It includes a combination of uppercase and lowercase letters. It also includes numbers. The specific characters are chosen deliberately. They enhance the security of the identifier. The length of the string also contributes to its security. Longer strings are more difficult to crack through brute-force attacks. The security of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is paramount.
The Role of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ in Online Services
AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ plays a critical role in various online services. It is particularly important in services that require user authentication. These might include services like APIs. They might also include cloud services. It acts as a gatekeeper. It grants access to specific functionalities. Without this key, access is often restricted. This protects the service from unauthorized use. This also protects sensitive data. The function of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is essential.
Consider the example of a web application. The application uses an API. The API allows access to data or features. AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ would be required. It would be required to authenticate the user. It would also be used to authorize the user’s access. The API would verify the identifier. It would determine if the user is permitted to use the service. This process is fundamental to modern web development.
Security Considerations for AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ
The security of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is of utmost importance. This is due to its critical role in access control. It is essential to protect it from unauthorized access. This is crucial to prevent misuse. This will prevent any potential security breaches. Several measures are employed to secure these identifiers. These measures are designed to enhance their integrity.
One of the most important measures is to keep AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ confidential. It should not be shared publicly. It should not be stored insecurely. It should be protected against unauthorized access. If the identifier is compromised, the associated service becomes vulnerable. This can lead to significant security risks. This includes data breaches. It also includes financial losses.
Regularly reviewing and updating access controls is another important step. This includes rotating AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ periodically. It also includes revoking access when necessary. These practices limit the potential damage from compromised identifiers. Implementing multi-factor authentication can also improve security. It adds an extra layer of protection. This makes it more difficult for attackers to gain access.
Best Practices for Managing AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ
Effective management of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is key to maintaining security. This involves several best practices. These best practices should be followed to protect the identifier. They should also protect the services it unlocks.
Always store AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ securely. Do not hardcode it into applications. Use environment variables. Use secure configuration files. These methods protect the identifier. They also prevent accidental exposure. Regularly monitor the usage of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ. This helps detect any unusual activity. This helps detect potential misuse. Implement robust logging. Log all access attempts. This provides an audit trail. This makes it easier to identify and respond to security incidents.
Regularly audit access permissions. Ensure only authorized users have access. Revoke permissions when necessary. These actions reduce the attack surface. They minimize the risk of unauthorized access. Educate your team about security best practices. This includes the importance of protecting AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ. Education promotes a security-conscious culture. This enhances overall security.
The Future of Identifiers like AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ
The digital landscape is constantly evolving. The methods used to authenticate and authorize access are also evolving. The future of identifiers, such as AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ, is likely to be shaped by advancements in technology. These include advancements in security protocols. These also include advancements in user authentication methods.
We can expect to see more sophisticated security measures. These will protect these critical identifiers. The use of multi-factor authentication will become more widespread. Biometric authentication will also gain prominence. These methods provide stronger protection. They make it more difficult for attackers to gain unauthorized access. The security of AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ will constantly evolve.
The rise of artificial intelligence may also play a role. AI can be used to detect and respond to security threats. It can also be used to automate security tasks. This helps protect identifiers. It also helps protect the services they secure. Understanding the evolution of these identifiers is crucial. It helps to maintain and enhance online security.
Conclusion
AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ is a vital element of the digital world. It is used for authentication and authorization. Its significance cannot be overstated. Its security is of utmost importance. Understanding its role is key. Following best practices is essential. Staying informed about evolving security threats is also crucial. This will secure valuable online resources. It will also protect sensitive data. By understanding the importance of identifiers like AIzaSyA28hkiOB3OeosdOfXueokFUKhB43X6gjQ, we can contribute to a safer and more secure online environment. This is crucial for the future.
[See also: Related Article Titles]